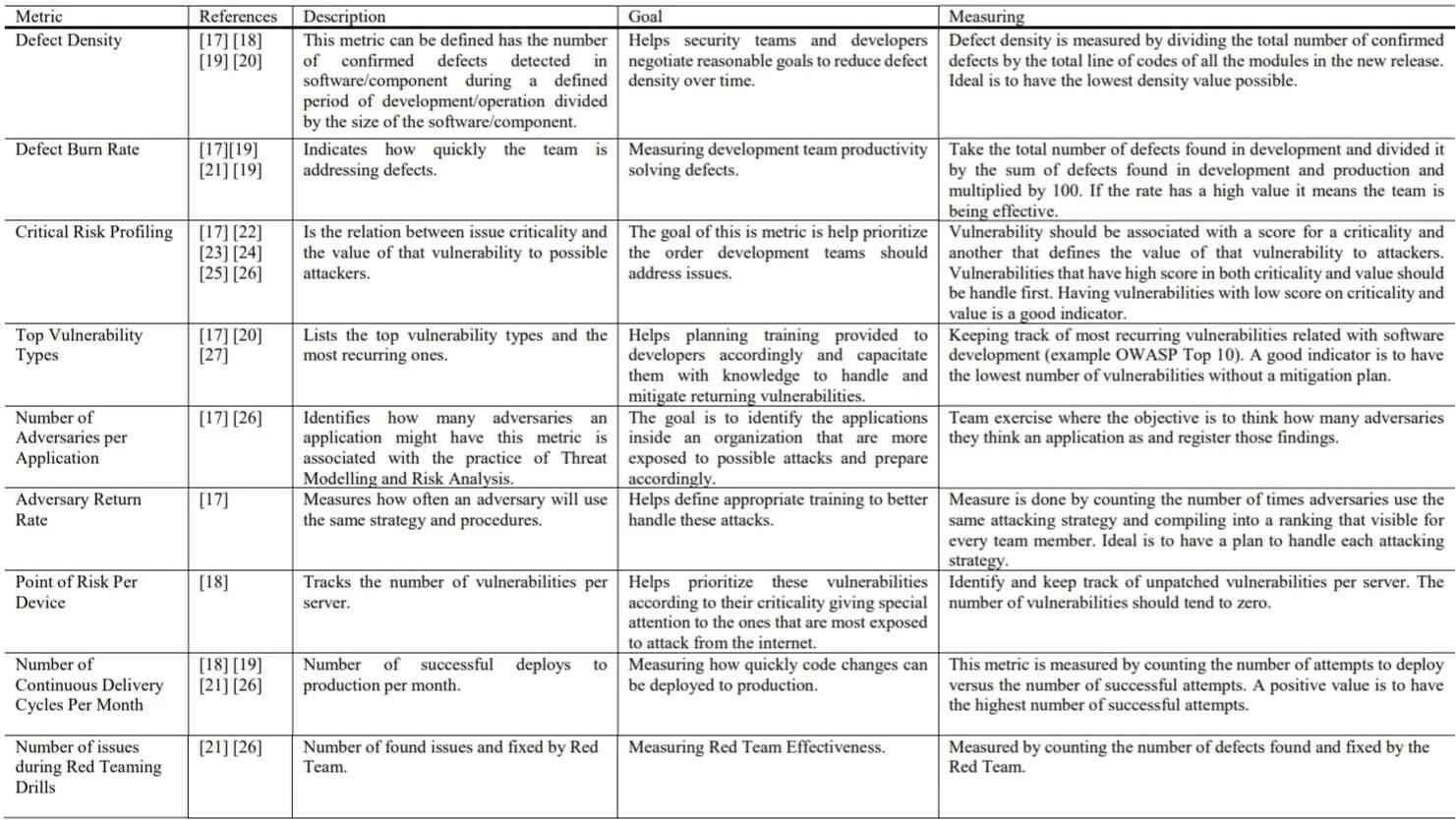
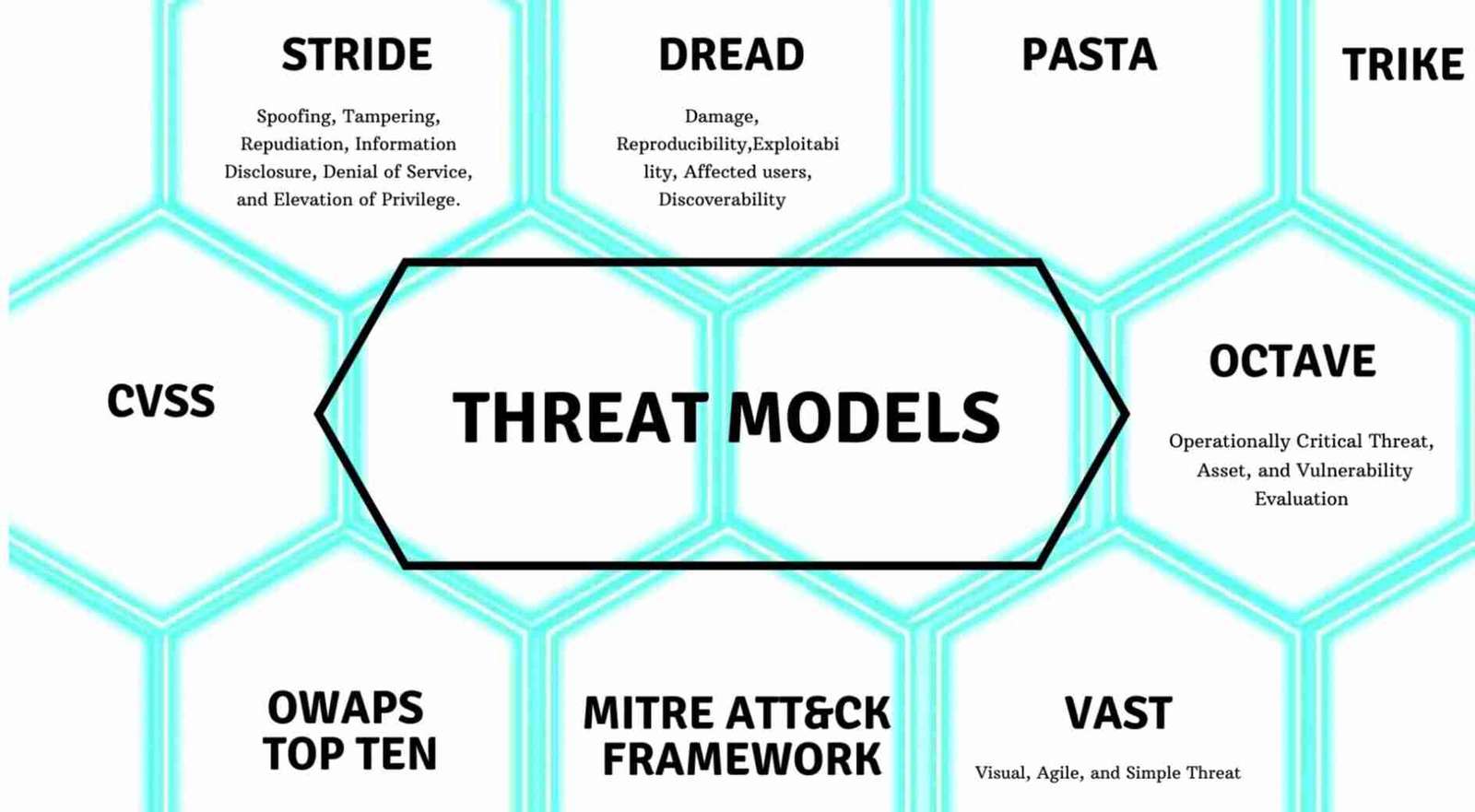
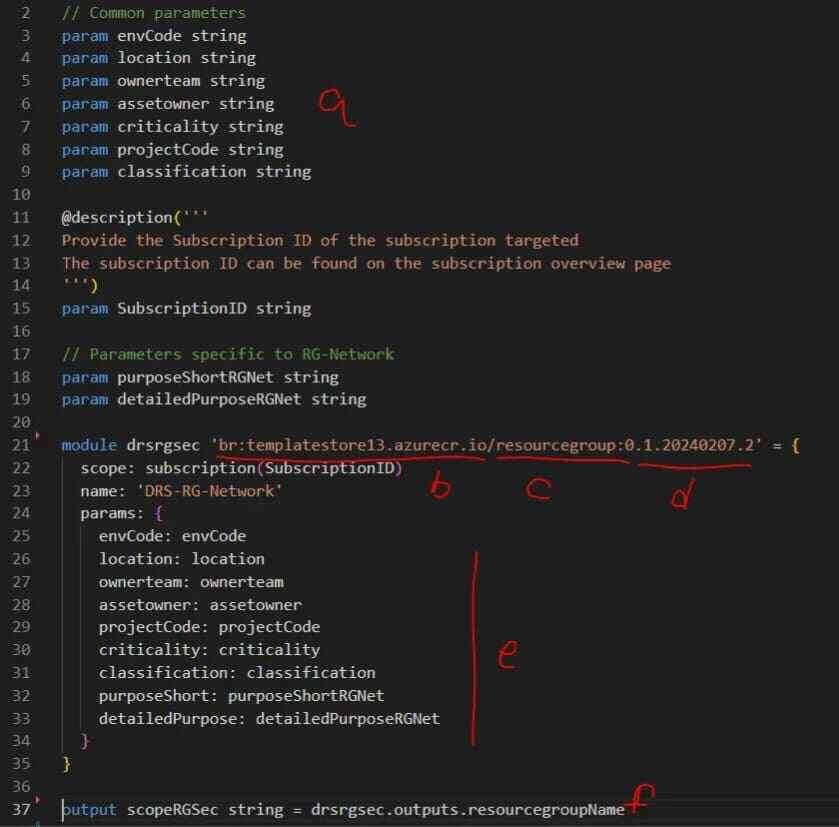
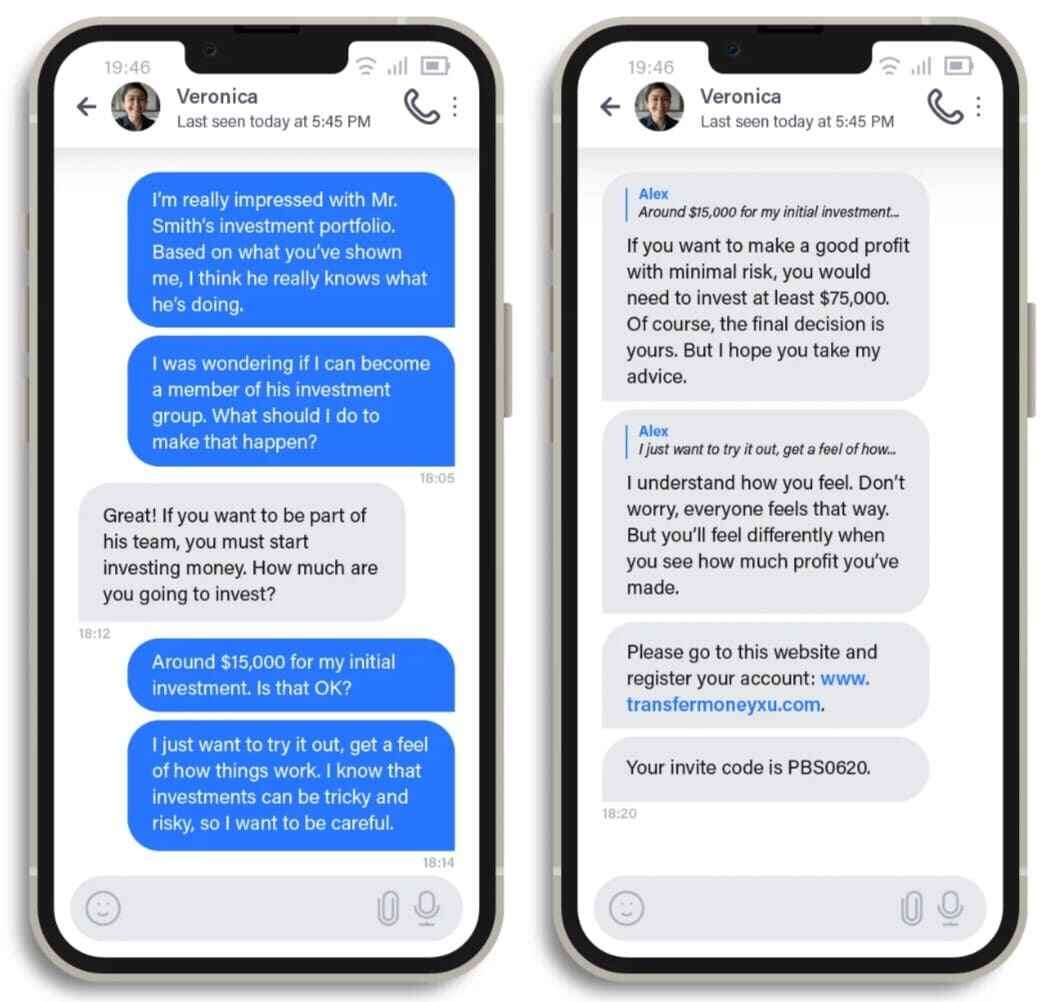
Senior Cloud & Security Architect | Microsoft Certified Trainer | Public Speaker
With over 17 years of experience, I design and deliver secure, scalable, and cloud-native solutions across the public sector, energy, transport, and finance industries. My expertise spans Azure, Kubernetes, Terraform, DevSecOps, and enterprise cloud governance.
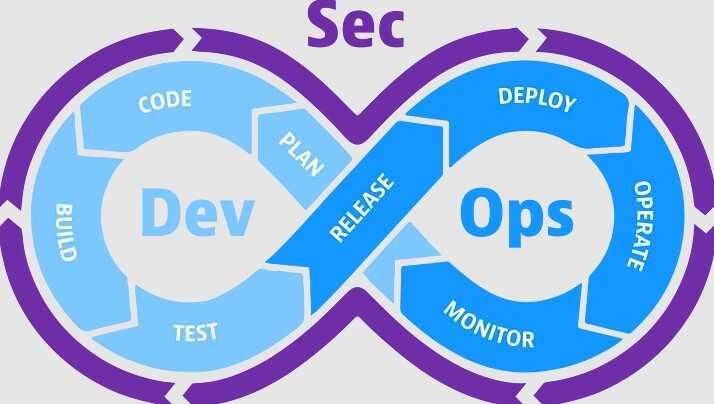
I’ve led large-scale cloud transformations and data center migrations, guiding organizations from legacy infrastructure to modern cloud environments. I focus on automation-first strategies—implementing Infrastructure as Code, CI/CD pipelines, and containerized workloads to enhance speed, reliability, and compliance.
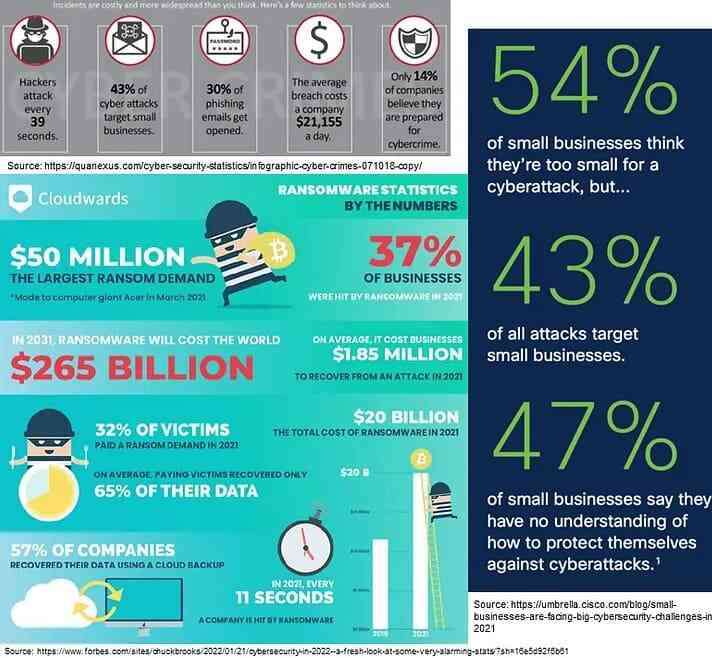
Security and governance are at the core of my work. I architect Zero Trust frameworks, integrate GDPR-compliant controls, and develop DevSecOps pipelines that bring together innovation and resilience across hybrid and multi-cloud ecosystems.
As a technical leader and mentor, I enjoy building high-performing teams and aligning technology strategy with business outcomes. My approach combines deep technical insight with collaboration, ownership, and continuous learning.
Outside of projects, I’m an active speaker and educator, sharing insights on cybersecurity, AI, and secure automation at global events including ISC2 Security Congress and the Nordic Infrastructure Conference.
Let’s connect if you’re driving secure innovation, scaling cloud platforms, or building impactful engineering teams.